An Incident like CrowdStrike’s Will Happen Again
In light of the recent CrowdStrike outage that has impacted tens of millions of computers and disrupted numerous industries worldwide, Xiid’s CTO, Federico Simonetti, contributes a unique perspective on this incident. As a lifelong ethical hacker who authored key anti-terrorism software for intelligence services and a former university professor specializing in advanced network protocols and secure operating systems, Simonetti’s experience reframes the CrowdStrike outage as a symptom of a wide-reaching, dangerous problem in cybersecurity rather than just a single, bad mistake. What follows is his opinion.
The Incident and Its Implications
The outage, caused by a defective CrowdStrike kernel driver update for Windows hosts, has led to widespread disruptions across the aviation, banking, healthcare, and other critical sectors. Affected systems experienced the dreaded “blue screen of death,” forcing many organizations to quickly resort to manual processes and emergency recovery measures with varying degrees of success.
While CrowdStrike has released a hotfix to prevent further propagation of the issue to systems that haven’t yet received the faulty update yet, this historic incident — perhaps the worst of its kind in history — is not the result of a one-off mistake. Instead, this is merely a symptom of two concerning cybersecurity trends that have been taking over the industry as of late:
The frequent circumvention of fundamental OS kernel design principles, leading to catastrophic consequences
The abuse of probabilistic AI as a one-size-fits-all solution, including cybersecurity tasks where absolute determinism is necessary
Circumventing Kernel Driver Signing Requirements
CrowdStrike’s circumvention of Microsoft’s kernel driver signing requirements was a glaring issue.
This inherently dangerous approach bypasses essential security mechanisms designed to prevent unauthorized or malicious code from running at the kernel level. When something goes wrong — as with CrowdStrike — the recovery process is usually exceedingly complex, often requiring physical access to the system to boot into safe mode and manually delete problematic files. This is not just an inconvenience; it poses a significant risk to system integrity and security. This is precisely what has just taken half of the world offline in the past few days.
So, what happened?
For kernel drivers, Microsoft requires a digital signature with a certificate that’s co-signed by Microsoft and the vendor and is only signed after Microsoft has extensively tested the driver in various conditions in their labs. If a driver is not signed in this way, it shouldn’t be loaded or executed by the operating system.
CrowdStrike’s main driver is signed exactly in this manner. The problem is that the signed driver then loads “update files” which do not only contain passive data (e.g. malware signatures) but also include additional code that the main driver executes. These additional files don’t go through the same extensive tests and digital co-signature as the main driver.
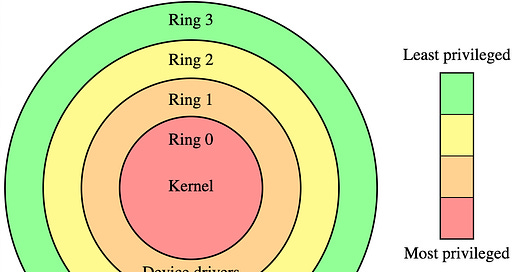
Since CrowdStrike operates at the Ring 0 level, a single botched update to one of these files can result in unrestricted code execution in your own operating system’s kernel. This is extremely risky and more dangerous than most malicious attacks.

The correct implementation, from an operating systems design perspective, is to keep the digitally signed driver “as is”, disallowing it from extending its own code by injecting updates into its kernel space, and instead running all detection logic (and updates) in user space, where a problematic update can only crash a single program — not the entire OS.
The kernel driver would then acquire all the data to be processed at kernel-space, where it can’t be affected by malware itself, switch context to user-space for analysis, validate its own user-space analysis tool to ensure it’s not compromised, and then receive the results of the analytical process back into the kernel-space via another context-switch.
This communication between kernel-space and user-space can be rendered non-tamperable by a process of mutual certificate verification between the kernel driver and the analysis program running in user-space.
While context-switching would necessarily be slower than doing everything in the kernel, a bad update would not have ground the world to a halt for the past 2 days if CrowdStrike’s had instead implemented this design philosophy. Operating systems would have kept running, and a simple additional hot-fix automatic update could have fixed everything.
The Role of Observability and AI in Cybersecurity
Observability is a critical component of detection frameworks like CrowdStrike’s Falcon platform. However, it is questionable whether this is the best approach in the current cybersecurity landscape.
AI-based analysis, while powerful, is non-deterministic by nature. In cybersecurity, absolute determinism is paramount; we cannot afford to hopethat a threat is detected — we must know that it is prevented. Heavy reliance on AI for threat detection introduces a level of uncertainty that can lead to catastrophic failures, as seen in this incident. These approaches are also reactionary, trying to respond quickly to threats that are detected after the intrusion has already occurred. It creates a race condition between the IT/InfoSec teams and the malicious intruder to close the security threat before significant damage is wrought.
Proactive security by design that prevents the intrusion from occurring is a far more desirable and effective approach to protecting digital infrastructure.
The Need for Deterministic Security Enforcement
The CrowdStrike incident makes it clear that we need to shift our focus towards more deterministic security solutions.
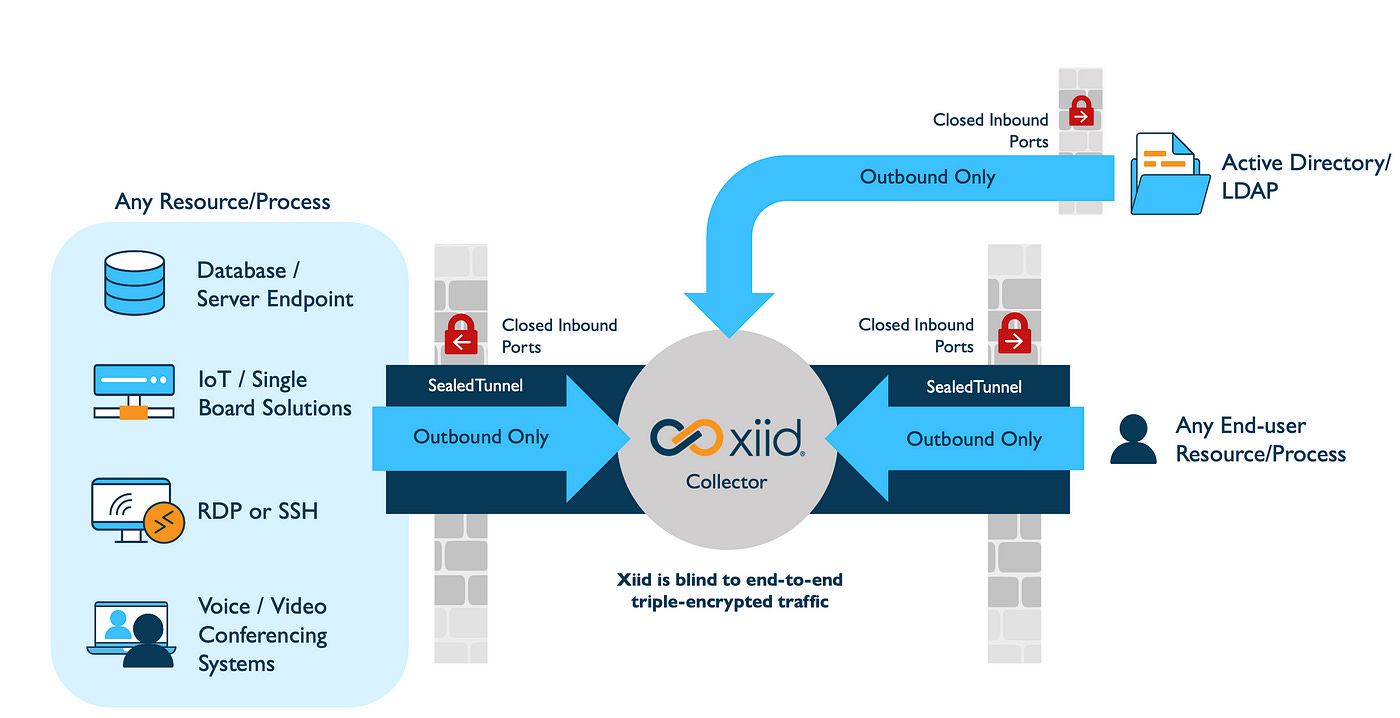
SealedTunnel™ offers a deterministic approach to security by establishing process-to-process, triple-encrypted, mutually verified networking tunnels. SealedTunnel eliminates the need for NAT and port forwarding, allowing firewalls to be completely closed to inbound traffic.
SealedTunnel’s architecture ensures that both endpoints (which are individual processes, not entire systems) connect outbound-only, which eliminates the possibility of an external attack. If an endpoint cannot be reached, it cannot be attacked. This is a fundamental shift from traditional security models that rely on detecting and mitigating threats after they have breached the perimeter.
The three layers of encryption used by SealedTunnel includes two mutual identity verifications, one of which uses a post-quantum secure key encapsulation mechanism (Kyber) and digital signature (Dilithium). This guarantees that no man-in-the-middle (MITM) or break-and-inspect attacks are possible. By integrating post-quantum cryptographic techniques, SealedTunnel not only addresses current security threats but also future-proofs against the rise of quantum computing threats, and prevents “Harvest Now, Decrypt Later” attacks that are becoming increasingly common.
SealedTunnel goes far beyond zero trust requirements, embodying the world’s first and only true zero-knowledge networking architecture. In this model, security is not an afterthought but is built into the core architecture by design. The deterministic nature of SealedTunnel’s security framework means that its functional model is absolute and not based on a case-by-case analysis. All endpoints protected by SealedTunnel can never be reached from outside of the SealedTunnel itself.
This approach provides a level of security that is both robust and reliable, ensuring that threats are prevented by design, rather than merely detected and reacted upon. This also reduces computational overhead by several orders of magnitude when compared with AI analysis for detection and reaction, improving performance.
Since all of this security is achieved without operating at the Ring 0 kernel level, a bug in Xiid’s software will never lead to a CrowdStrike-style incident.
Analysis and detection tools are still a good safeguard to have, should any threat reach an endpoint via another authorized endpoint, but the use of SealedTunnel offloads a significant amount of work and computation from these analysis tools that are located further down in a multi-layered security perimeter.
As a result, deterministic solutions like SealedTunnel and well-implemented AI-based detection like CrowdStrike can synergistically benefit each other, and ultimately the end user, who would enjoy a predictable level of protection and a “smart” level of detection for the cases that are not deterministically covered by other methods.